Traboda partnered with a leading health-tech company to secure their digital ecosystem and protect sensitive patient data. The engagement involved penetration testing of four critical web applications, a public-facing Android application, and the supporting cloud infrastructure for web and Android app. By identifying vulnerabilities and delivering actionable recommendations, Traboda enhanced the security of these assets, ensuring secure access to sensitive information and compliance with industry standards. This work reinforced the company’s commitment to delivering secure and reliable healthcare technology solutions.
About the client
The company develops cutting-edge health-tech solutions centered on remote health monitoring. Its device and cloud-based systems integrate biosensor technology with mobile applications, enabling real-time health data collection and remote diagnostics. By combining convenience with clinical accuracy, it plays a key role in the digital transformation of healthcare.
Challenges
Complex Ecosystem: The client’s digital ecosystem included multiple interconnected web applications, an Android app, and cloud infrastructure. Each component required both individual and integrated testing to identify vulnerabilities while minimizing disruption to ongoing operations.
Highly Sensitive Data: The applications managed sensitive patient health data, including real-time cardiac monitoring information. This required stringent adherence to ethical testing practices to ensure data privacy and regulatory compliance throughout the engagement.
Time Constraints: The pentesting engagement needed to be completed within a limited timeframe due to the impending deployment of new features in the web and mobile applications. This necessitated prioritizing testing strategies to focus on the highest-risk areas.
Legacy and Modern Components: The system included a mix of modern technologies and legacy components, some of which lacked adequate documentation. Identifying vulnerabilities in those older components required significant manual analysis and reverse engineering.
Unsecured APIs: APIs exposed critical functionality but lacked standardized security practices, such as authentication and authorization. Testing these endpoints without impacting live operations posed additional challenges.
Compliance Considerations: The client needed to align with healthcare-specific regulations like HIPAA while addressing broader security concerns, such as those outlined in the OWASP Top 10. This required a balance between regulatory and technical security requirements.
Objectives
Identify and Remediate Vulnerabilities: Perform a thorough security assessment of the web applications, Android app, and cloud infrastructure to uncover and prioritize vulnerabilities for remediation.
Ensure Data Privacy and Compliance: Ensure the client’s systems comply with industry standards and regulatory requirements (e.g., HIPAA), protecting sensitive patient data from unauthorized access or misuse.
Strengthen API Security: Evaluate the security of exposed APIs to identify gaps in authentication and authorization mechanisms, ensuring these critical components are resilient to attacks.
Evaluate Component Integrity: Identify outdated or vulnerable components in the technology stack and recommend upgrades to ensure robust application security.
Establish a Secure Foundation: Provide actionable recommendations and a roadmap for long-term security improvements, including secure development practices, regular testing, and automated scanning tools.
Minimize Operational Impact: Perform all testing with minimal disruption to the client’s live services, ensuring uninterrupted availability of critical healthcare applications.
Methodology
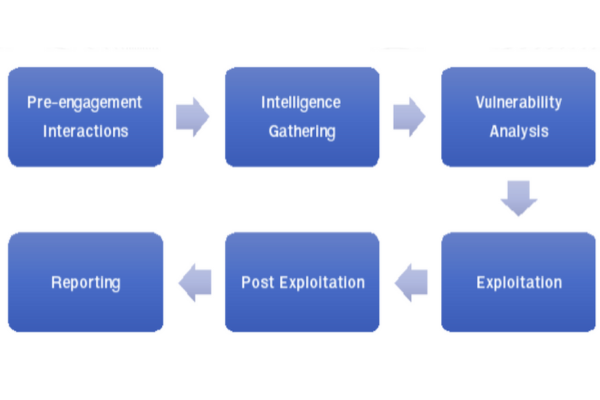
Pre-engagement Interactions
Traboda conducted a kick-off meeting with the client to align expectations for the engagement. During the meeting, the agreed-upon scope was reviewed, additional information was gathered, and any IPs or URLs that required whitelisting by the client were identified.
Intelligence Gathering
Intelligence Gathering, also known as Reconnaissance, is the initial phase aimed at evaluating the current maturity level of the targets within the scope. This stage offers valuable insights into how to proceed with the engagement based on the current security posture of the targets. Open-source intelligence (OSINT) will be utilized to gather additional information about the target and name the target uniquely.
Vulnerability Analysis
In this stage, the goal is to identify the flaws and weaknesses of the targets within the scope that a potential attacker could exploit. This phase will be conducted using a combination of automated tools and manual testing, aiming to identify all the vulnerabilities that could be exploited by a potential attacker.
Exploitation
The Exploitation stage goes beyond just identifying vulnerabilities; it focuses on determining whether the discovered vulnerabilities can be exploited and if they can be leveraged to launch an attack on the target. The objective of this stage is to simulate an attack environment that a potential attacker might employ to compromise the target.
Post Exploitation
The inclusion or exclusion of this stage is determined based on the scope agreement established during the pre-engagement interactions. The objective of this stage is to assess the criticality and potential impact of a successful exploitation from an attacker’s perspective.
Summary of Findings
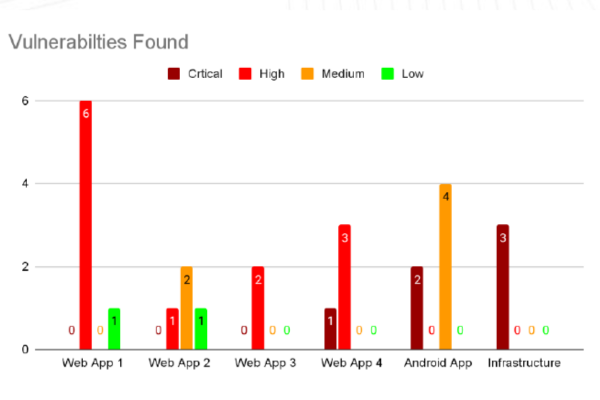
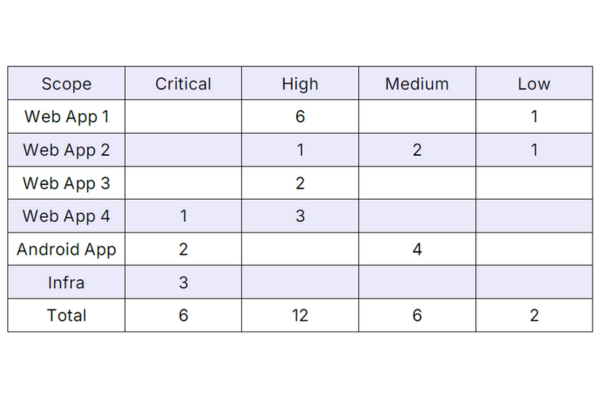
Result and Impact
Critical Vulnerabilities Addressed
- Identified and mitigated 6 critical vulnerabilities, including default credentials, vulnerable components, and missing API authorization.
- Prevented potential exploitation scenarios that could have led to unauthorized access, data breaches, and service disruptions.
Risk Reduction
- Discovered a total of 26 vulnerabilities (6 critical, 12 high, 6 medium, and 2 low).
- Enabled the company to prioritize fixes, starting with the most critical and high-impact vulnerabilities, ensuring efficient allocation of resources.
Strengthened API Security
Highlighted significant gaps in API authorization mechanisms, ensuring these endpoints were secured to prevent unauthorized access to sensitive data.
Improved Infrastructure Security
Addressed misconfigurations in the cloud environment, reducing exposure to remote exploitation and improving compliance with secure deployment practices.
Enhanced Application Security
Mitigated risks stemming from the use of outdated third-party components, preventing potential exploitation of known vulnerabilities.
The cloud infrastructure and applications were thoroughly tested for security vulnerabilities using custom test cases. The vulnerabilities found were reported and fixed. A subsequent retest confirmed that the vulnerabilities were effectively resolved, significantly strengthening the organization’s application and infrastructure security.




